Cloud Orchestrated Services for MObile Security (COSMOS)
The last few years have witnessed an explosive growth in the number of personal mobile devices, such as smart phones and tablets. This growth has been followed by an even more exceptional increase in the download of mobile applications. Unfortunately, security threats have rapidly expanded along with the diffusion of personal mobile applications. Since mobile devices usually host highly sensitive personal information, application security has become a primary concern for mobile users. Approaches targeted to application security in traditional desktop environments such as malware and virus detection, and information leak detection are computationally expensive, thus not suitable for mobile devices, as they would impact on both responsiveness and battery lifetime. In this context, the cloud computing paradigm can be leveraged to offload security-oriented functions from the devices to the cloud infrastructure. Furthermore, mobile applications can be encapsulated in a virtual environment in the cloud, and transparently accessed by mobile users through a remote connection. In any case, value-added services can be provided by the cloud provider to improve mobile application security.
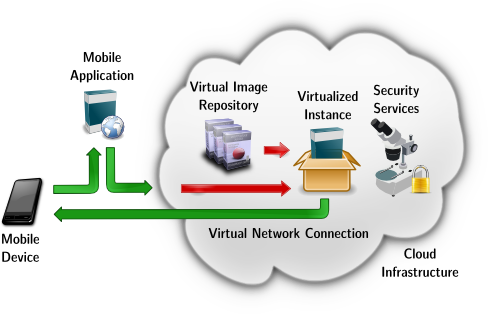
Architecture of the COSMOS system
Example of Secure Mobile Cloud Computing
In this project, we propose COSMOS (Cloud Orchestrated Services for MObile Security), a cloud-based system for securing applications running on mobile devices will be designed and implemented. It will lead to the definition of a cloud infrastructure and framework specifically tailored to mobile devices and focused on application security. This new infrastructure will be able to support heterogeneous devices in terms of both architectures and platforms, and will leverage virtualization to provide services for securing mobile applications. Mechanisms for resource-efficient service access and provisioning will be investigated at the mobile devices and at the cloud infrastructure, respectively. As for mobile devices, low-overhead and mobility-aware protocols and algorithms will be developed with the goal of improving the user experience in terms of device battery lifetime and system responsiveness. As for the cloud infrastructure, a software layer for allocation and management of secure virtual environments will be implemented, as well as a flexible framework for security-oriented services.
Secure Virtual Environment to host and manage mobile applications
Research Activity
In the previous projects we developed system architectures and tools for high-availability resource allocation in a grid-based cloud infrastructure, mechanisms for detection and prevention of attacks in cloud environments (even with mobile nodes), and a situation-aware framework to support secure ubiquitous applications in the cloud. Our solutions also provide cross-layer services in terms of policies, risks and cost analysis, and Quality of Service (QoS) support. We plan to build on that work towards the definition of a virtualized cloud infrastructure targeted to mobile applications.
This project is funded by National Science Foundation under Grant No. CNS-1404677.
Faculty
- Prof. Sajal K. Das
- Dr. Debraj De
PhD Students
- Mayank Raj
- Rakesh Kumar
- Pratool Bharti
Publications
Journals and book chapters
- M. Raj, M. Di Francesco, S. K. Das, Secure Mobile Cloud Computing, Handbook on Securing Cyber-Physical Critical Infrastructure, February, 2012
Conferences
- N. Roy, C. Julien and S. K. Das, "Resource-optimized quality-assured ambiguous context mediation in pervasive environments," Proceedings of the The 6th International ICST Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness (QShine 2009), November, 2009 (link)
Keynote and Invited Talks
- M. Di Francesco, Exploiting Cloud Computing to Secure Mobile Applications; in Panel: Security and Privacy in Mobile Cloud Computing, the 2nd IEEE International Workshop on Data Security and PrivAcy in wireless Networks (D-SPAN), Lucca, Italy, June 2011
- S. K. Das, Pervasive Secure Infrastructures (PSI): Integrating Smart Sensing, Data Mining, Pervasive Networking and Community Computing; European Wireless Symposium, Lucca, Italy, Apr 2010; IEEE Int'l Conf on Intelligence and Security Informatics (ISI), Dallas, June 2009
Ph.D Dissertations
- Pallapa, Gautham V., "A Privacy Enhanced Situation-aware Middleware Framework For Ubiquitous Computing Environments," Ph.D dissertation, Comp. Sc. & Engg. Dept., Univ. of Texas at Arlington, Arlington, Texas, 2010 (link)
- Roy, Nirmalya, "A Context-aware Learning, Prediction And Mediation Framework For Resource Management In Smart Pervasive Environments," Ph.D dissertation, Comp. Sc. & Engg. Dept., Univ. of Texas at Arlington, Arlington, Texas, 2008 (link)

Follow Computer Science