CPS SECURITY Project
Acknowledgement:
“This material is based upon work supported by the National Science Foundation under Grant No. CNS-1545050.”
Disclaimer:
"Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation.”
Award numbers (collaborative awards)
URL: https://www.nsf.gov/awardsearch/showAward?AWD_ID=1545050
Duration (expected): September 1, 2015 – August 31, 2020
Award Title: CPS: TTP Option: Synergy: Collaborative Research: Threat Assessment Tools for Management-Coupled Cyber- and PhysicalInfrastructures
PI: Sajal K. Das
Postdoc(s): Shameek Bhattacharjee, Francesco Betti Sorbelli
Student(s): Venkat Praveen Madhavarapu, Sudharsan Vaidhun and Prithwiraj Roy
Project Goals
Strategic decision-making for physical-world infrastructures is rapidly transitioning toward a pervasively cyber-enabled paradigm, in which human stakeholders and automation leverage the cyber-infrastructure at large (including on-line data sources, cloud computing, and handheld devices). This changing paradigm is leading to tight coupling of the cyber- infrastructure with multiple physical- world infrastructures, including air transportation and electric power systems. These management-coupled cyber- and physical- infrastructures (MCCPIs) are subject to complex threats from natural and sentient adversaries, which can enact complex propagative impacts across networked physical-, cyber-, and human elements.
The goals of this multi-university collaborative project are to develop models, frameworks and tools for assessing threats in interdependent cyber-physical systems (CPS) with human in the loop. Specific goals include:
- Modeling threat landscape in interdependent CPS networks;
- Developing trust models for secure decision making in presence of adversarial threats;
- Designing effective strategies for threat mitigation.
The developed models and tools are applied to secure different network infrastructures that aim to reduce failures and threat propagation in cyber-physical-human systems. The underlying CPS and loT networks involve sensor, drone and UAV networks; and mobile crowd sensing platforms. The developed solutions are being applied to air traffic systems.
The project will also train postdocs, graduate and undergraduate students in the multidisciplinary areas of cyber-physical-human systems, mobile crowd sensing, and cyber-physical security.
Major Activities and Findings
The project has made substantial progress by developing novel frameworks and solutions for some fundamental problems that serve as building blocks for threat assessment and attack mitigation in human-coupled CPS. Our research solved the following problems, leading to several high quality journal and peer-reviewed conference papers, as summarized later.
Securing Wireless Sensors, Drones and UAV Networks
Wireless sensor networks (WSN), drones and unmanned aerial vehicles (UAV), or opportunistic networks form some of the important communication infrastructures for cyber-physical systems (CPS) and Internet of Things (loTs). However, they are often vulnerable to various kinds of attacks, such as jamming, intrusions, consensus, and denial of service. We proposed novel frameworks and solutions to protect against jamming attacks in WSNs, consensus attacks in UAV networks, and localization errors in drones.
Specifically, we analyzed structural perspective of computational effectiveness for quantized consensus in layered UAV networks (published in IEEE Transactions on Control of Network Systems, Mar 2019); and novel range based algorithms for precise localization of terrestrial objects using drones (published in Pervasive and Mobile Computing, 2018).
We also proposed a distributed shuffling scheme to protect against selective jamming attacks in IEEE 802.15.4e based sensor networks (published in ACM Transaction on Sensor Networks, Feb 2019); and further quantified risks to authorize collaborative requests (ACM ASIACCS, July 2019).
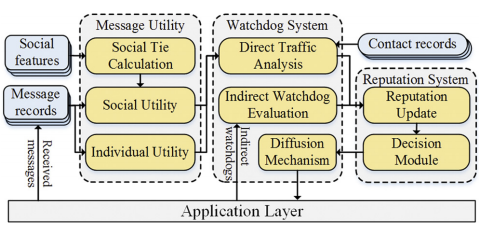
For opportunistic mobile networks, we developed a social-based watchdog system to detect selfish nodes (Future Generation Computer Systems, Jan 2019); and for next generation challenged networks under adverse conditions, we proposed a novel communication architecture (IEEE INFOCOM, May 2019).
Trust Models for Secure Decision Making in CPS and IoTs
We have proposed novel trust models and frameworks for secure decision making in CPS and loTs against data integrity attacks, such as false data injection. The novelty lies in a newly defined information theoretic metric composed of harmonic mean to arithmetic mean ratio, which provides a stable invariant under various attacks. This approach resulted in an innovative anomaly detection framework that is applicable to multiple CPS networks (e.g., smart grid and smart transportation). Efforts are on the way to apply this framework to air traffic systems.
We established harmonic mean to arithmetic mean ratio as a stable invariant (and developed the corresponding theory) to effectively detect anomalies in stealthy data falsification in times series data following a non-stationary Gaussian distribution, with application to smart metering infrastructure in smart grid (IEEE Transactions on Dependable and Secure Computing, 2019).
lncentivization and Reputation Scoring in Mobile Crowd Sensing to Prevent Selfish or Malicious Intent
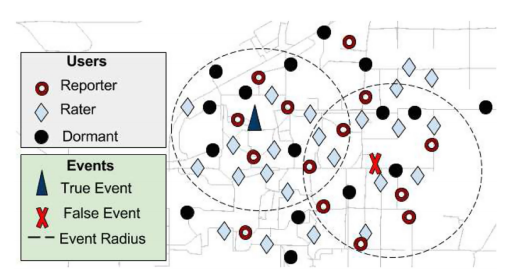
Mobile Crowd Sensing (MCS) applications may generate false reports due to malicious intent, thus impacting the dependability and reliability of the CPS infrastructures. We proposed a novel reputation model, based on trust scores and incentives of users and their loT devices, to be able to classify genuine or malicious behaviors with high degree of accuracy and minimum false alarms. This method has been effectively applied to vehicular CPS, for example.
For defending against false reports in mobile crowd sensing, significant results are derived for vehicular CPS (ACM Transactions on Cyber-Physical Systems, 2019). Further, we developed a unified approach based on quality and quantity metrics for secure and trustworthy decision making (IEEE Transactions on Mobile Computing, 2019).
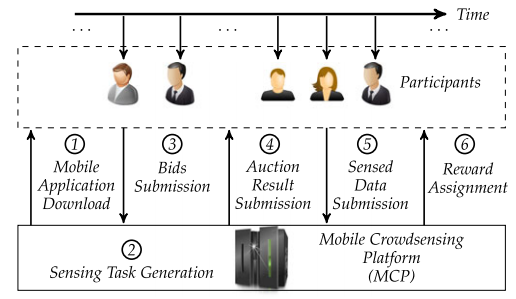
As regards to incentivization mechanisms in mobile crowd sensing based loT systems, several contributions are made to optimize reliable information collection with high quality. The works appeared in IEEE Transactions on Mobile Computing (July 2019); ACM Transactions on Sensor Networks (Feb 2019); and IEEE Internet of Things Journal (June 2019).
Selected Publications
Books
- S. Roy and S. K. Das (2020). Principles of Cyber-Physical Systems: An Interdisciplinary Approach, Cambridge University Press. ISBN: 978-1-10706661-8.
Book Chapters
- A. Pratap and S. K. Das (2020). “Internet of Things in 5G Cellular Networks: Radio Resource Perspective,” Internet of Things and Secure Smart Environments: Success and Pitfalls (Eds: U. Ghosh and R. Datta), CRC Press.
- P. S. Paul, K. Hazra, S. Saha, S, Nandi, S. Chakraborty, and S. K. Das (2017). “Generating Crisis Maps for Large-scale Disasters: Issues and Challenges,” Wireless Public Safety Networks (Eds. D. Camara and N. Nikae), Vol. 3, Chapter 4, Springer.
Refereed Journals
- F. B. Sorbelli, C. M. Pinotti, S. Silvestri, and S. K. Das (2021). “Measurement Errors in Range-based Localization Algorithms for UAVs: Analysis and Experimentation,” IEEE Transactions on Mobile Computing, to appear.
- F. B. Sorbelli, F. Coro, S. K. Das, and C. M. Pinotti (2021). “Energy-Efficient Delivery of Goods with Drones under Varying Wind Conditions,” IEEE Transactions on Intelligent Transportation Systems (special issue on Unmanned Aircraft System Traffic Management), to appear.
- S. Bhattacharjee and S. K. Das (2021). “Detection and Forensics against Stealthy Data Falsification in Smart Metering Infrastructure,” IEEE Transactions on Dependable and Secure Computing, to appear.
- S. Bhattacharjee, V. K. P. Madhavarapu, S. Silvestri, and S. K. Das (2021). “Attack Context Embedded Data Driven Trust Diagnostics in Smart Metering Infrastructure,” ACM Transactions on Privacy and Security, to appear.
- R. P. Barnwal, N. Ghosh, S. K. Ghosh, and S. K. Das (2020). “Publish or Drop Traffic Event Alerts? Quality-aware Decision Making in Participatory Sensing-based Vehicular CPS,” ACM Transactions on Cyber-Physical Systems (Special Issue on Transportation Cyber-Physical Systems). 4 (1), 9:1-9:28.
- S. Bhattacharjee, N. Ghosh, V. K. Shah, and S. K. Das (2020). “QnQ: Quality and Quantity based Unified Approach for Secure and Trustworthy Mobile Crowdsensing,” IEEE Transactions on Mobile Computing. 19 (1): 200-216.
- A. Sturaro, S. Silvestri, M. Conti, and S. K. Das (2020). “A Realistic Model for Failure Propagation in Interdependent Cyber-Physical Systems,” IEEE Transactions on Network Science and Engineering (Special Issue on Network Science for High-Confidence Cyber-Physical Systems), 7 (2): 817-837.
- S. Kumar and S. K. Das (2020). “Target Detection and Localization Methods using Compartmental Model for Internet of Things,” IEEE Transactions on Mobile Computing, 19 (9), 2234-2249.
- A. Pal, M. Raj, K. Kant, and S. K. Das (2020). “A Smartphone based Network Architecture for Post-Disaster Operations using WiFi Tethering,” ACM Transactions on Internet Technology, 20 (1), 6:1-6:27.
- H. Vasudev, V. Deshpande, D. Das, and S. K. Das (2020). “A Lightweight Mutual Authentication Protocol for V2V Communication in Internet of Vehicles,” IEEE Transactions on Vehicular Technology, 69 (6): 6709-6717.
- T. Limbasiya, D. Das, and S. K. Das (2020). “MComIoV: Secure and Energy-Efficient Message Communication Protocols for Internet of Vehicles,” IEEE/ACM Transactions on Networking, under revision, 2020.
- Y. Wan, J. Yan, Z. Lin, V. Sheth, and S. K. Das (2019). “On the Structural Perspective of Computational Effectiveness for Quantized Consensus in Layered UAV Networks,” IEEE Transactions on Control of Network Systems. 6 (1): 276-288.
- B. Jedari, F. Xia, H. Chen, S. K. Das, A. Tolba, and Z. Al-Makhadmeh (2019). “A Social-based Watchdog System to Detect Selfish Nodes in Opportunistic Mobile Networks,” Future Generation Computer Systems, 92: 777-788.
- F. Restuccia, P. Ferraro, S. Silvestri, S. K. Das, and G. Lo Re (2019). “IncentMe: Effective Mechanism Design to Stimulate Crowdsensing Participants with Uncertain Mobility,” IEEE Transactions on Mobile Computing, 18 (7): 1571-1784.
- F. Restuccia, P. Ferraro, T.S. Sanders, S. Silvestri, S. K. Das, and G. Lo Re (2019). “FIRST: A Framework for Optimizing Information Quality in Mobile Crowdsensing Systems,” ACM Transactions on Sensor Networks, 15 (1), 5:1-5:31.
- M. Tiloca, D. De Guglielmo, G. Dini, G. Anastasi and S. K. Das (2019). “DISH: Distributed Shuffling against Selective Jamming Attack in IEEE 802.15.4e TSCH Networks, ACM Transactions on Sensor Networks, 15 (1), 3:1-3:28.
- T. T. Luo, J. Huang, S. S. Kanhere, J. Zhang, and S. K. Das (2019). “Improving IoT Data Quality in Mobile Crowdsensing: A Cross Validation Approach,” IEEE Internet of Things Journal, 6 (3), 5651-5664.
- F. B. Sorbelli, S. K. Das, C. M. Pinotti, and S. Silvestri (2018). “Range based Algorithms for Precise Localization of Terrestrial Objects using a Drone,” Pervasive and Mobile Computing, 48: 20-42.
- S. Saha, S. Nandi, R. Verma, S. Sengupta, K. Sing, V. Sinha, and S. K. Das (2018). “Design of Efficient Lightweight Strategies to Combat DoS Attack in Delay Tolerant Network Routing,” Wireless Networks, 24 (1), 173-194.
- F. Restuccia, N. Ghosh, S. Bhattacharjee, S. K. Das, and T. Melodia (2017). Quality of Information in Mobile Crowdsensing: Survey and Research Challenges. ACM Transactions on Sensor Networks. 13 (4), 34:1-34:43.
- A. De Paola, P. Ferraro, S. Gaglio, G. Lo Re and S. K. Das (2017). “An Adaptive Bayesian System for Context-Aware Data Fusion in Smart Environments.” IEEE Transactions on Mobile Computing, 16 (6): 1502-1512.
- L. Cheng, J. Niu, L. Kong, C. Luo, Y. Gu, W. He, and S. K. Das (2017). “Compressive Sensing based Data Quality Improvement for Crowd-sensing Applications,” Journal of Network and Computer Applications, 77: 123-134.
- M. Tiloca, D. De Guglielmo, G. Dini, G. Anastasi, and S. K. Das (2017). “JAMMY: A Distributed and Self-Adaptive Solution against Selective Jamming Attack in TDMA WSNs,” IEEE Transactions on Dependable and Secure Computing, 14 (4): 392-405.
- N. Marchang, R. Dutta, and S. K. Das (2017). “A Novel Approach for Efficient Usage of Intrusion Detection System in Mobile Ad Hoc Networks,” IEEE Transactions on Vehicular Technology, 66 (2): 1684-1695.
- T. Luo, S. S. Kanhere, J. Huang, S. K. Das, and F. Wu (2017). “Sustainable Incentives for Mobile Crowdsensing: Auctions, Lotteries, Trust and Reputation Systems,” IEEE Communications Magazine (special issue on Sustainable Incentive Mechanisms for Mobile Crowdsensing), 55 (3): 68-74.
- F. Restuccia and S. K. Das (2016). “Optimizing the Lifetime of Sensor Networks with Uncontrollable Mobile Sinks and QoS Constraints,” ACM Transactions on Sensor Networks, 12 (1).
- T. Luo, S. K. Das, H.-P. Tan, and L. Xia (2016). “Incentive Mechanism Design for Crowdsourcing: An All-Pay Auction Approach,” ACM Transactions on Intelligent Systems and Technology, 7 (3): 1-26.
- F. Restuccia, S. K. Das, and J. Payton (2016). “Incentive Mechanisms for Participatory Sensing: Survey and Research Challenges,” ACM Transactions on Sensor Networks, 12 (2).
- T. Luo, S. S. Kanhere, S. K. Das, and H.-P. Tan (2016). “Incentive Mechanism Design for Heterogeneous Crowdsourcing Using All-Pay Contests,” IEEE Transactions on Mobile Computing, 15 (9), 2234-2246.
Juried Conference Papers
- M. Chen, W. Liang, and S. K. Das (2021). “Data Collection Utility Maximization in UAV-enabled Sensor Networks via Judiciously Determining Hovering Locations,” 19th IEEE International Conference on Pervasive Computing and Communications (PerCom).
- A. Khochare, Y. Simmhan, F. B. Sorbelli, and S. K. Das (2021). “Heuristic Algorithms for Co-scheduling of Edge Analytics and Routes for UAV Fleet Missions.” IEEE International Conference on Computer Communications (INFOCOM).
- F. De Vita, D. Bruneo, and S. K. Das (2020). “A Novel Data Collection Framework for Telemetry and Anomaly Detection in Industrial IoT Systems,” ACM/IEEE Conference on Internet of Things Design and Implementation (IoTDI), pp. 245-251.
- G. Lingam, R. R. Rout, D. V. L. N. Somayajulu, and S. K. Das (2020). “Social Botnet Community Detection: A Novel Approach based on Behavioral Similarity in Twitter Network using Deep Learning,” 15th ACM ASIA Conference on Computer and Communications Security (ASIACCS).
- J. Vyas, D. Das, and S. K. Das (2020). “Vehicular Edge Computing based Driver Recommendation System Using Federated Learning,” 17th IEEE International Conference on Mobile Ad Hoc and Sensor Systems (MASS).
- S. Halder, M. Conti, and S. K. Das (2020). “COIDS: A Clock Offset Based Intrusion Detection System for Controller Area Networks,” 21st ACM International Conference on Distributed Computing and Networking, 22:1-22:10.
- S. Vaidhun, Z. Guo, J. Bian, H. Xiong, and S. K. Das (2020). “Priority-based Multi-Flight Path Planning with Uncertain Sector Capacities” 12th International Conference on Advanced Computational Intelligence (ICACI), pp. 529-535.
- K. Hazra, V. K. Shah, M. Bilal, S. Silvestri, S. K. Das, S. Nandi, and S. Saha (2019). “A Novel Network Architecture for Resource-Constrained Post-Disaster Environments,” 11th IEEE International Conference on Communication Systems and Networks (COMSNETS),, 328-335.
- N. Ghosh, R. Singhal, and S. K. Das (2019). “R2Q: A Risk Quantification Framework to Authorize Requests in Web-based Collaborations,” 14th ACM Asia Conference on Information, Computer and Communications Security (ASIACCS). 247.
- V. K. Shah, S. Roy, S. Silvestri, and S. K. Das (2019). “Towards Energy-efficient and Robust Disaster Response Networks,” International Workshop on Emergency Response Technologies and Services (EmeRTeS). 397.
- V. K. Shah, S. Silvestri, B. Luciano, and S. K. Das (2019). “X-CHANT: A Diverse DSA based Architecture for Next-generation Challenged Networks,” IEEE International Conference on Computer Communications (INFOCOM), pp.586-594.
- V. K. Shah, S. Roy, S. Silvestri, and S. K. Das (2019). “Bio-DRN: Robust and Energy-efficient Bio-inspired Disaster Response Networks,” 16th IEEE Int’l Conference on Mobile Ad-hoc and Smart Systems (MASS).
- Z. Guo, K. Yang, S. Vaidhun, S. Arefin, S. K. Das, and H. Xiong (2018). “Uniprocessor Mixed-Criticality Scheduling with Graceful Degradation by Completion Rate,” 39th IEEE Real-Time Systems Symposium (RTSS), pp. 373-383.
- D. Wu, J. Li, S. K. Das, J. Wu, Y. Ji and Z. Li (2018). “Novel Distributed Denial-of-Service Attacks Detection for Software Defined Networking Environments,” IEEE International Conference on Communications (ICC).
- F. B. Sorbelli, C. M. Pinotti, S. Silvestri, and S. K. Das (2018). “On the Accuracy of Localizing Terrestrial Objects Using Drones,” IEEE International Conference on Communications (ICC).
- F. B. Sorbelli, S. K. Das, C. M. Pinotti, and S. Silvestri (2018). “Precise Localization in Sparse Sensor Networks using a Drone with Directional Antennas,” 19th ACM International Conf. on Distributed Computing and Networking (ICDCN).
- S. Roy, A. Tamimi, A. Hahn, M. Xue, S. K. Das, H. Van Dongen, A. Vosughi, and S. Warnick (2018). “A Modeling Framework for Assessing Cyber Disruptions and Attacks to the National Airspace System,” AIAA Modeling and Simulation Technologies Conference.
- S. Vaidhun, S. Arefin, Z. Guo, H. Xiong, and S. K. Das (2017). “Response Time in Mixed-Critical Pervasive Systems,” 14th IEEE International Conference on Ubiquitous Intelligence and Computing (UIC).
- V. K. Shah, S. Roy, S. Silvestri, and S. K. Das (2017). “CTR: Cluster based Topological Routing for Disaster Response Networks,” IEEE International Conference on Communications (ICC).
- S. Bhattacharjee, N. Ghosh, V. K. Shah, and S. K. Das (2017). “QnQ: A Reputation Model to Secure Mobile Crowdsourcing Applications from Incentive Losses,” IEEE Conference on Communications and Network Security (CNS).
- A. Sturaro, S. Silvestri, M. Conti, and S. K. Das (2016). “Towards a Realistic Model for Failure Propagation in Interdependent Networks,” International Conference on Computing, Networking and Communications (ICNC).
- F. Restuccia, A. Saracino, S. K. Das, and F. Martinelli (2016). “LVS: A WiFI-based System to Tackle Location Spoofing in Location-based Services,” IEEE Symposium on a World of Wireless Mobile Multimedia Networks (WoWMoM).
- R. Barnwal, N. Ghosh, S. Ghosh, and S. K. Das (2016). “Enhancing Reliability of Vehicular Participatory Sensing Network: A Bayesian Approach,” 2nd IEEE International Conference on Smart Computing (SMARTCOMP).
Broader Impacts
The project develops practical schemes and analyses to tie special infrastructure-network features to security/vulnerability. As a central case study, the framework and tools will be used for threat assessment and risk analysis of CPS networks. Three canonical types of threats are addressed: environmental-to-physical threats, cyber-physical co-threats, and human-in-the-loop threats. This case study will help develop and deploy software decision aids for managing man-made disturbances to the air traffic system
The research conducted in this project motivates students, including female and under-represented minority, to choose careers in the nationally important area of cyber-physical security. A postdoctoral researcher and two Ph.D. students are trained in cutting-edge research dealing with CPS security. They published several important papers. One Ph.D. student graduated in June 2019. The postdoc became an Assistant Professor of Computer Science at Western Michigan University.
For outreach and community building effort, a successful workshop on Big Data and loT Security (BITS) was organized in conjunction with IEEE SMARTCOMP conference (www.smart-comi;1.org) in 2017-2019. PI Das collaborated with Japanese colleagues to organize this workshop. Another tangible outcome of this project is that Das established new research collaboration with Vanderbilt University and Japan that led to a successful collaborative project, called STEAM, funded by the NSF and NICT in Japan under JUNO2 program. Thus the CPS project acted as a catalyst for further international collaboration including visit exchanges by colleagues and students across partner institutions.
Point of Contact: Sajal K. Das (sdas@mst.edu)
Date of last Update: December 29, 2020

Follow Computer Science